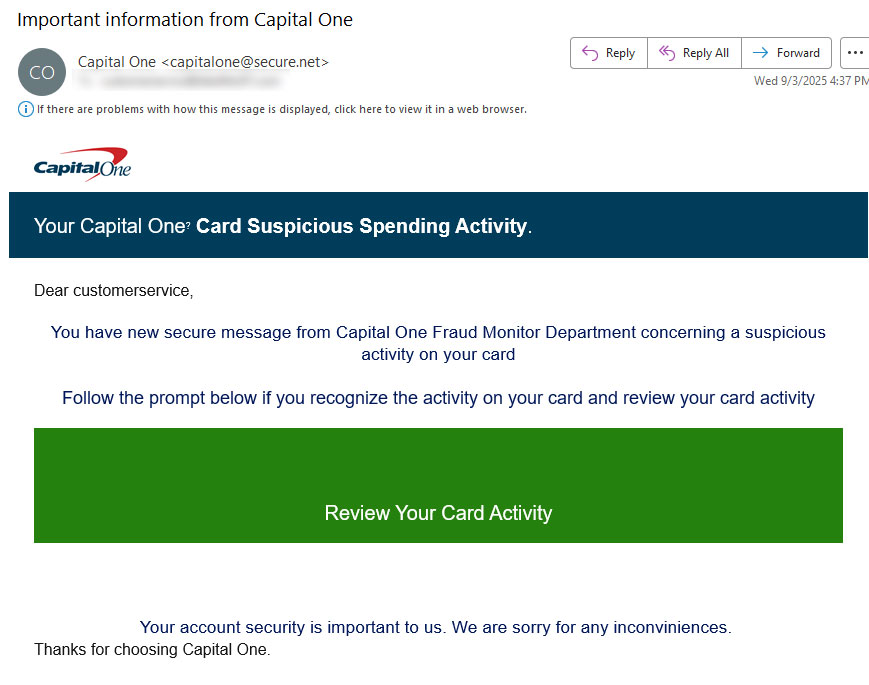
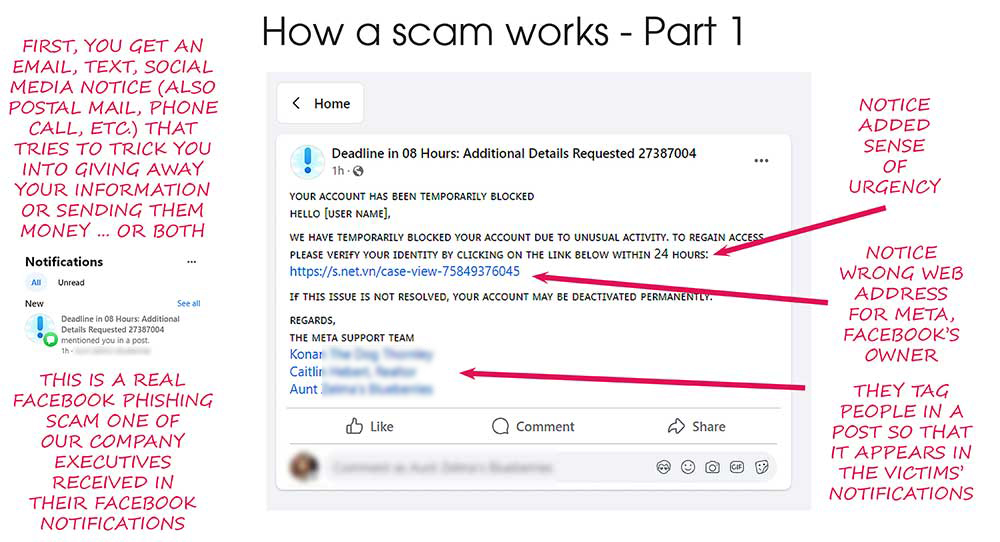
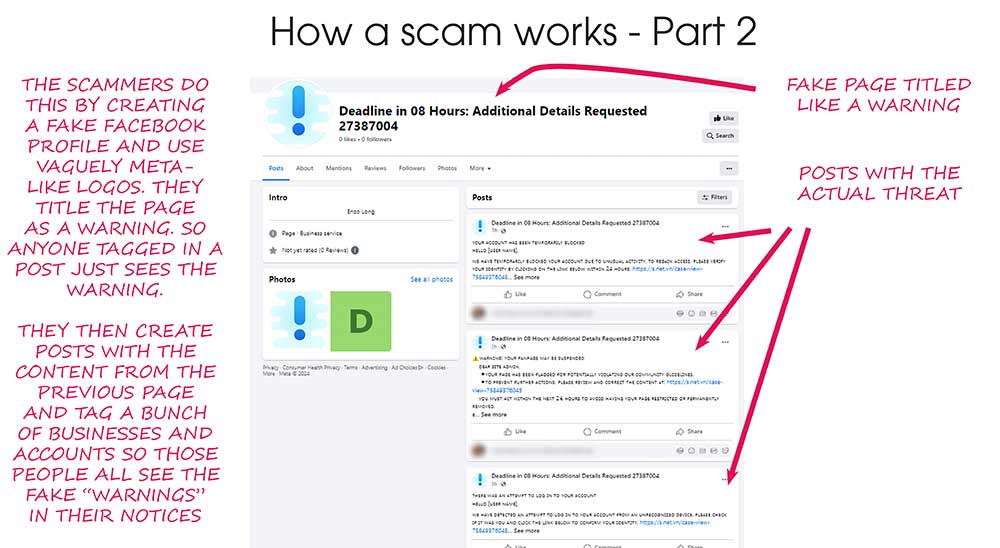
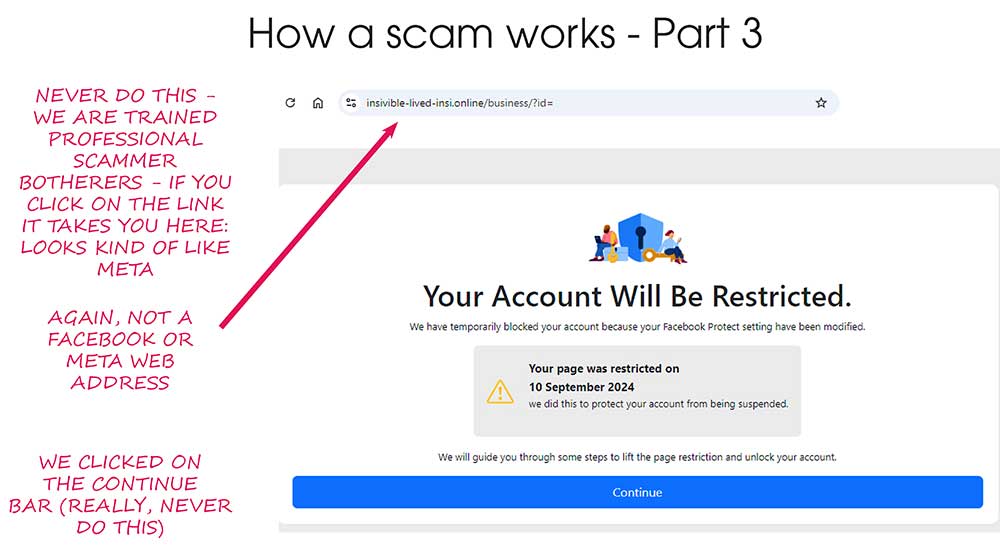
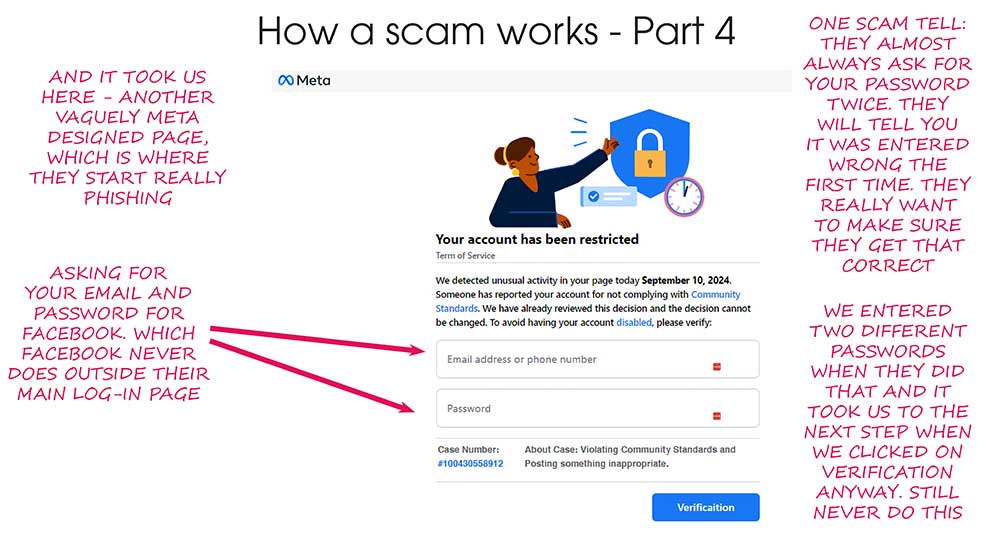
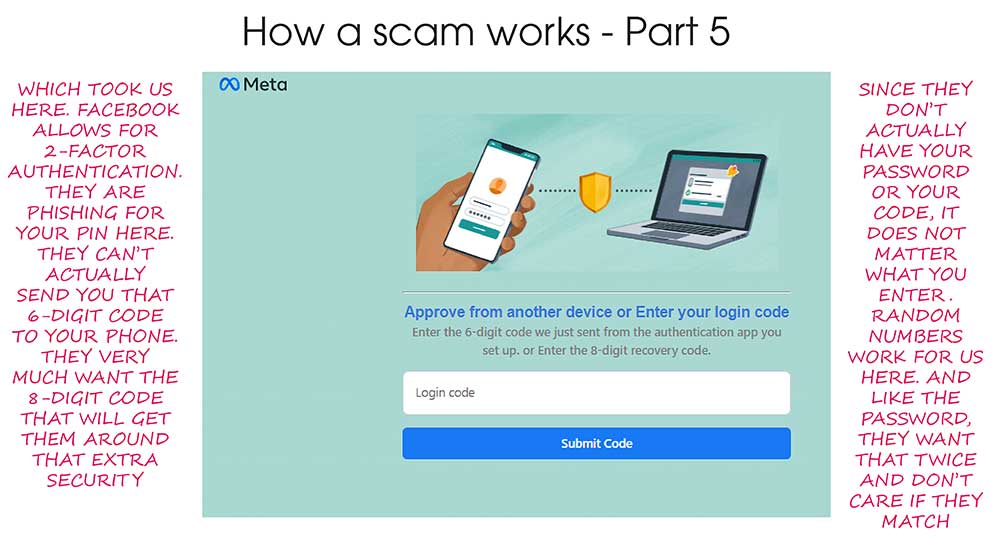
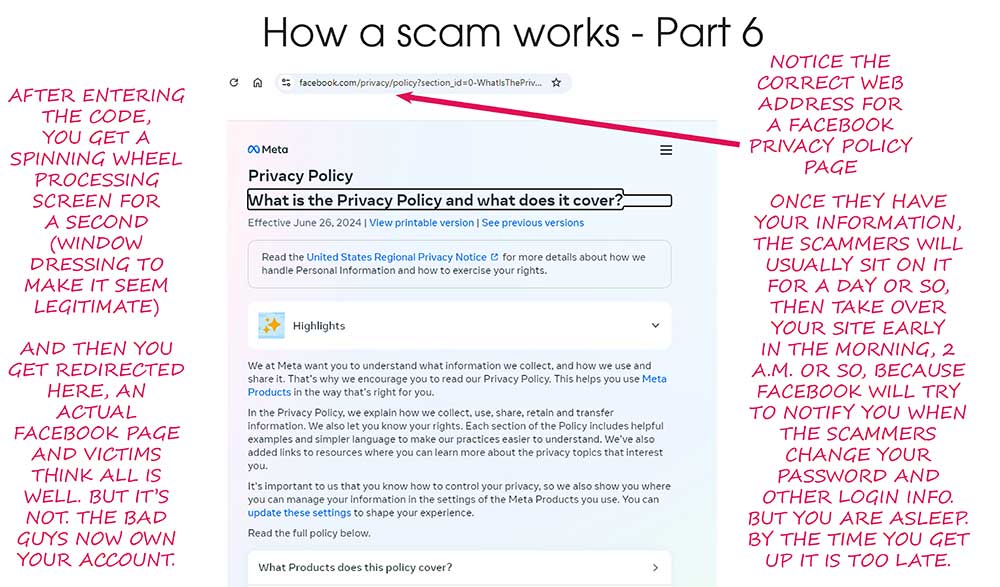
I’ve been getting this phishing email about twice a day lately, and at first glance it looks pretty convincing. It’s designed to look like a security warning from Capital One — but don’t be fooled.
What makes this one different? Unlike most scams, it doesn’t immediately try to scare you with threats like “your account will be shut down” or “act now or lose access.” Instead, it takes a sneakier approach.
The New Trick They’re Using
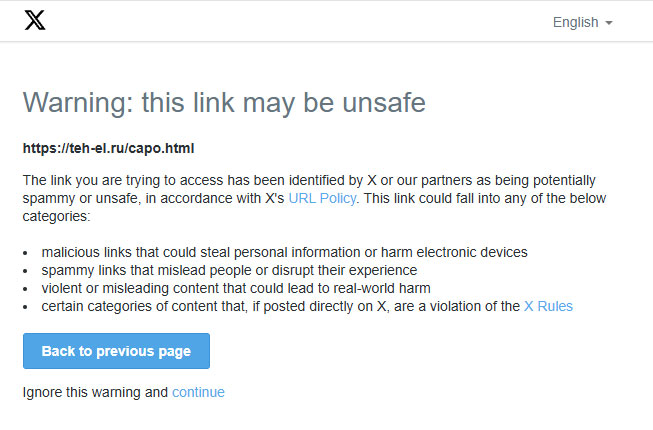
The email has a button labeled “Review Your Card Activity.” If you hover over the link, here’s the surprise:
- It doesn’t take you straight to a shady website.
- Instead, it runs through Twitter/X first, then redirects to another site.
- Twitter does flash a warning screen — which is good — but if they know it’s a scam, why not just remove it?
That’s the frustrating reality: social media platforms are slow to remove scam content, even when they know it’s fake.
Who Actually Stopped It
Here’s the good news: the hosting company where the final fake login page lived shut it down almost immediately after it was reported.
That’s why reporting phishing emails matters.
- Social media may not act quickly,
- but hosting companies usually do.
- Reporting helps get the actual phishing pages taken offline, so fewer people can fall for them.
What You Can Do to Stay Safe
Don’t rely on platforms. Social media won’t always protect you — but you can protect yourself.
Hover before you click. Always check where a link really goes.
Be suspicious of redirects. If a link bounces through multiple sites, that’s a red flag.
Report it. Forward phishing emails to reportphishing@apwg.org or report directly to the company being spoofed.